 Let me start with something that might surprise you: implementing zero-trust architecture isn’t about throwing out everything you’ve built and starting afresh. It’s about fundamentally changing how we think about security within our existing infrastructure. When we talk about zero-trust on Nutanix, we’re really discussing a journey rather than a destination.
Let me start with something that might surprise you: implementing zero-trust architecture isn’t about throwing out everything you’ve built and starting afresh. It’s about fundamentally changing how we think about security within our existing infrastructure. When we talk about zero-trust on Nutanix, we’re really discussing a journey rather than a destination.
The traditional approach to network security has been rather like building a fortress. We’ve focused on creating strong perimeter defences whilst assuming everything inside the walls can be trusted. Anyone who’s dealt with a lateral movement attack will tell you how spectacularly this approach can fail. Zero-trust flips this concept entirely: nothing is trusted by default, regardless of where it sits on the network.
Overview
- Why Nutanix Makes Zero-Trust Implementation Practical
- Building the Foundation: Starting with Identity
- Microsegmentation: The Heart of Zero-Trust
- Real-World Implementation: Learning from Experience
- Monitoring and Enforcement: Seeing What Matters
- Integration with Broader Security Tools
- The Journey Continues: Evolving Your Zero-Trust Implementation
- Practical Considerations and Common Pitfalls
- Measuring Success: What Good Looks Like
Why Nutanix Makes Zero-Trust Implementation Practical
Here’s where Nutanix becomes particularly interesting for zero-trust implementations. Unlike traditional infrastructures where you’re cobbling together solutions from multiple vendors, Nutanix provides an integrated platform that makes implementing zero-trust principles considerably less painful.
The hyperconverged nature of Nutanix means that compute, storage, and networking are already tightly integrated. This integration becomes a significant advantage when implementing zero-trust because you’re not trying to coordinate security policies across disparate systems. Everything speaks the same language, which makes policy enforcement and monitoring far more straightforward.
Building the Foundation: Starting with Identity
Every successful zero-trust implementation begins with identity, and this is where many organisations stumble. It’s not enough to simply integrate with Active Directory and call it done. You need to think about identity in the context of every connection, every transaction, and every piece of data access.
When setting up identity management within Nutanix, you’ll want to establish clear role boundaries from the start. Rather than creating broad administrative roles, think about what people actually need to do their jobs. A database administrator doesn’t need full cluster access; they need specific permissions to manage database workloads. An application owner needs to provision and manage their applications but shouldn’t have access to the underlying infrastructure configuration.
The beauty of Nutanix’s approach to identity management is how it integrates with existing identity providers whilst providing granular control over platform access. You can connect to Active Directory, LDAP, or SAML providers like Okta without having to maintain separate user databases. This integration extends beyond simple authentication to include authorisation policies that follow users as they access different parts of the platform.
Microsegmentation: The Heart of Zero-Trust
If identity is the foundation of zero-trust, microsegmentation is its beating heart. This is where Nutanix Flow Network Security really shines. Rather than relying on traditional VLANs or firewall rules, Flow allows you to create security policies based on application context and business logic.
The approach I’ve seen work best in practice is to start with discovery mode. Let Flow observe your traffic patterns for a few weeks before you start creating policies. This baseline period is crucial because it helps you understand the actual communication patterns in your environment, which are often quite different from what the documentation says should be happening.
See my post Traffic Discovery with Nutanix Flow Network Security to learn how:
During a recent implementation at a services firm, we discovered that their supposedly three-tier application was actually communicating across several different services and external APIs that nobody had documented. Without that discovery phase, we would have created policies that broke the application whilst leaving legitimate communication paths unprotected.
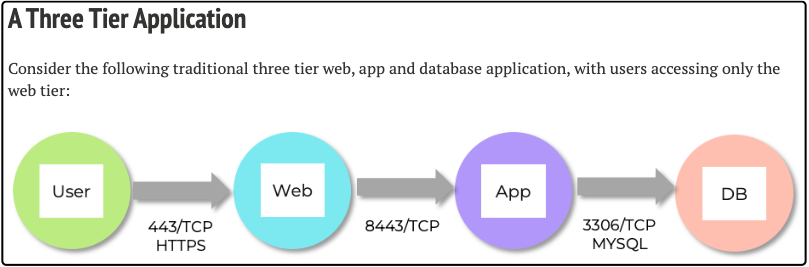
Once you understand your traffic patterns, creating policies becomes a matter of translating business requirements into network rules. For instance, if you have a customer-facing web application, you know that the web tier needs to communicate with the application tier, and the application tier needs database access. What you probably don’t want is direct communication between the web tier and the database, or any communication between production and development environments.
See my post Microsegmentation with Nutanix Flow Network Security to learn how:
Real-World Implementation: Learning from Experience
Let me share what I’ve learned from implementing zero-trust architectures on Nutanix across various organisations. The technical implementation is often the easy part; the cultural and operational changes are what typically cause the most challenges.
One company I worked with had been running a fairly open internal network for years. Their attitude was that if someone had access to the building and could plug into the network, they were probably authorised to be there. This approach worked reasonably well until they started connecting their operational technology to the same network as their business systems.
The zero-trust implementation on Nutanix allowed them to create clear boundaries between different types of systems without requiring a complete network redesign. We used Flow to create policies that ensured production control systems could only communicate with specific engineering workstations, whilst keeping business systems completely isolated from the manufacturing floor.
The key lesson from this implementation was the importance of starting small and building trust in the system. We began with non-critical development environments, proved that the policies worked as expected, and gradually expanded to cover production systems. This approach gave the operations team confidence in the technology whilst allowing them to understand how the new security model would affect their daily work.
Monitoring and Enforcement: Seeing What Matters
One of the most significant advantages of implementing zero-trust on Nutanix is the visibility you gain into your environment. Traditional network monitoring tools often provide either too much information or too little context. Nutanix provides application-aware monitoring that shows you not just what traffic is flowing, but what business purpose that traffic serves.
This visibility becomes crucial when you move from monitoring mode to enforcement mode. You need to understand not just what traffic is being blocked, but what impact that blocking has on business operations. The integrated monitoring in Nutanix makes this correlation much easier than trying to piece together information from multiple tools.
During the enforcement phase, you’ll likely discover communication patterns that weren’t visible during the discovery phase. This is particularly common with applications that have occasional batch processes or maintenance routines that don’t run during normal discovery periods. Having good monitoring in place allows you to quickly identify and address these issues without compromising security.
One such tool that can be used in this space is Security Central.
Integration with Broader Security Tools
Whilst Nutanix provides excellent native security capabilities, zero-trust architecture typically requires integration with broader security tools. You’ll want to connect Flow with your Security Information and Event Management (SIEM) system to correlate network security events with other security data. You might also want to integrate with threat intelligence feeds to automatically update policies based on emerging threats.
The API-driven nature of Nutanix makes these integrations relatively straightforward. When a vulnerability scanner identifies a compromised system, automated policies can immediately isolate that system whilst allowing security teams to investigate.
The Journey Continues: Evolving Your Zero-Trust Implementation
Implementing zero-trust architecture isn’t a project with a defined end date; it’s an ongoing process of refinement and improvement. As your applications evolve, as new threats emerge, and as your business requirements change, your zero-trust policies need to evolve as well.
The advantage of implementing zero-trust on Nutanix is that the platform grows with your requirements. As Nutanix continues to add new security capabilities and integrate with additional security tools, your zero-trust implementation becomes more sophisticated without requiring fundamental architectural changes.
What I’ve found most valuable is establishing regular reviews of your zero-trust policies. These reviews should include not just security teams, but application owners and business stakeholders. The goal is to ensure that your security policies continue to support business objectives whilst providing appropriate protection.
Practical Considerations and Common Pitfalls
Having implemented zero-trust architectures across various Nutanix environments, there are several common pitfalls I always warn organisations about. The first is trying to implement everything at once. Zero-trust is a significant change in how you approach security, and your teams need time to adapt to new processes and tools.
Another common mistake is focusing too heavily on the technology whilst ignoring the operational aspects. Zero-trust requires changes to how you provision new applications, how you troubleshoot network issues, and how you respond to security incidents. These process changes are often more challenging than the technical implementation.
Finally, don’t underestimate the importance of documentation and training. Your zero-trust policies need to be well-documented and your teams need to understand how to work within the new security model. This documentation becomes particularly important when you need to troubleshoot issues or when new team members join the organisation.
Measuring Success: What Good Looks Like
A successful zero-trust implementation on Nutanix should provide several measurable benefits. You should see a reduction in the potential blast radius of security incidents, improved visibility into application communication patterns, and greater confidence in your ability to detect and respond to threats.
From an operational perspective, you should find that security becomes more predictable and manageable. Rather than dealing with ad-hoc firewall rules and network access requests, you have clear policies that automatically enforce appropriate access controls.
Most importantly, zero-trust should make your organisation more resilient without making it less agile. The right implementation enhances your ability to deploy new applications and services securely, rather than creating barriers to business innovation.
The journey towards zero-trust architecture on Nutanix is ultimately about building a more secure, more resilient, and more manageable infrastructure. It’s a journey that requires commitment, patience, and a willingness to change established practices. However, the benefits in terms of security posture, operational efficiency, and business agility make it a worthwhile investment for organisations serious about modern cybersecurity.
-Chris